Mitigating Risks: Best Practices for Managing Legacy Device Security
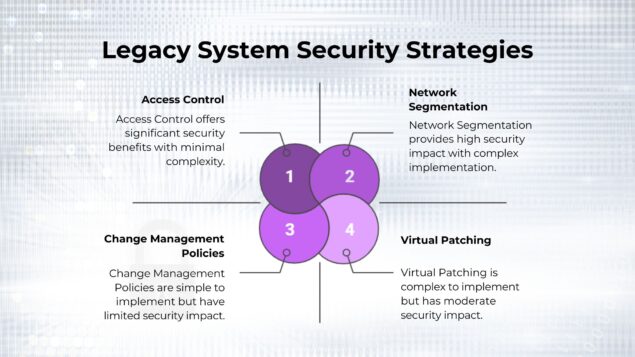
Best Practices for Managing Legacy Device Security Legacy devices are like time bombs ticking away quietly inside your IT infrastructure. While they may still function and perform business-critical operations, their outdated architecture and lack of modern defences make them highly attractive targets for cybercriminals. Legacy systems remain deeply embedded in operations from hospitals to financial…